Uploading Profiles to Private S3 Bucket
In some cases, customer security policies may prohibit them from uploading profiles directly to WhyLabs via the whylogs API. An alternative solution is to set up an S3 bucket owned by the customer to which profiles can be uploaded. WhyLabs can then retrieve profiles delivered to this bucket. This can be done with the following steps.
Create a cross-account IAM role
To create a new workspace, you must set up an IAM cross-account role so that WhyLabs can access your AWS account. This IAM role includes a policy that varies depending on your deployment type. The configuration procedure is the same for all options, regardless of policy.
Get your WhyLabs external ID. You need it when you create the AWS cross-account IAM role in your AWS account. Contact WhyLabs support if you don’t have access to this external ID.
Log into your AWS Console as a user with administrator privileges and go to the IAM service.
Click the Roles tab in the sidebar.
Click Create role.
a) In Select type of trusted entity, click the Another AWS account tile.
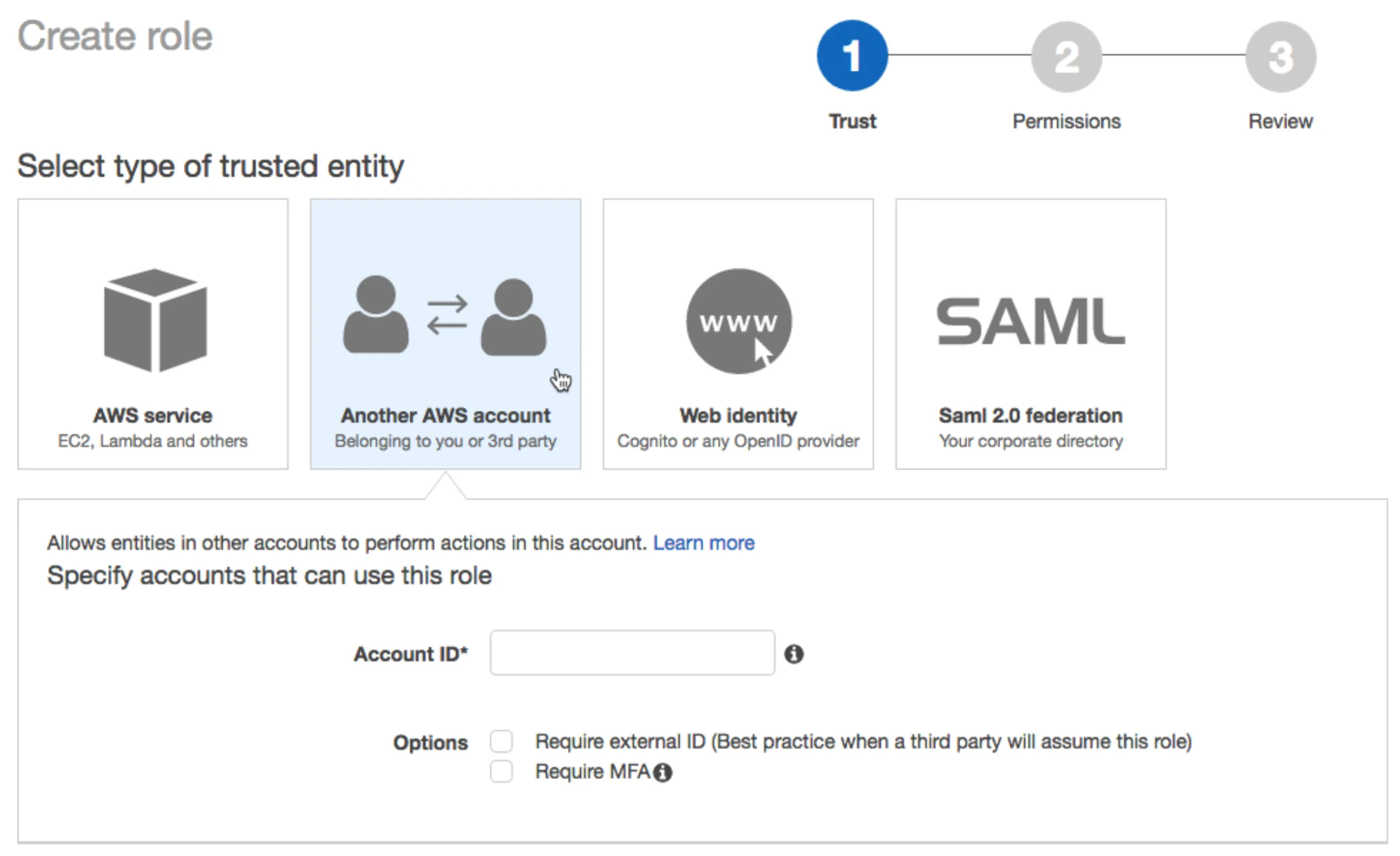
b) In the Account ID field, enter the WhyLabs account ID 003872937983. This is not the WhyLabs organization ID
c) Select the Require external ID checkbox.
d) In the External ID field, enter your WhyLabs external ID provided above. Protect your external ID like a credential.
e) Click the Next: Permissions button.
f) Click the Next: Tags button.
g) Click the Next: Review button.
h) In the Role name field, enter a role name.
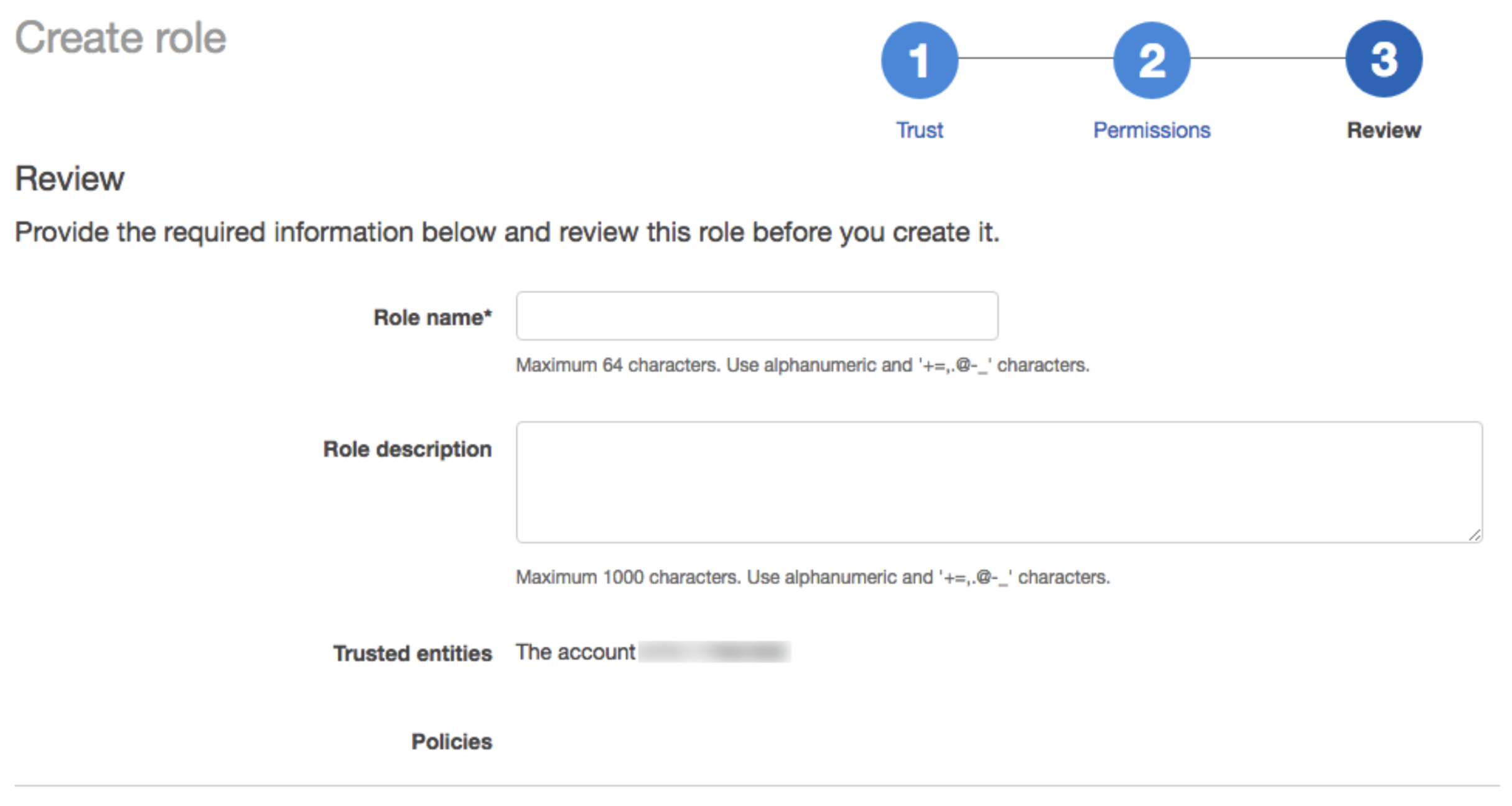
i) Click Create role. The list of roles displays.
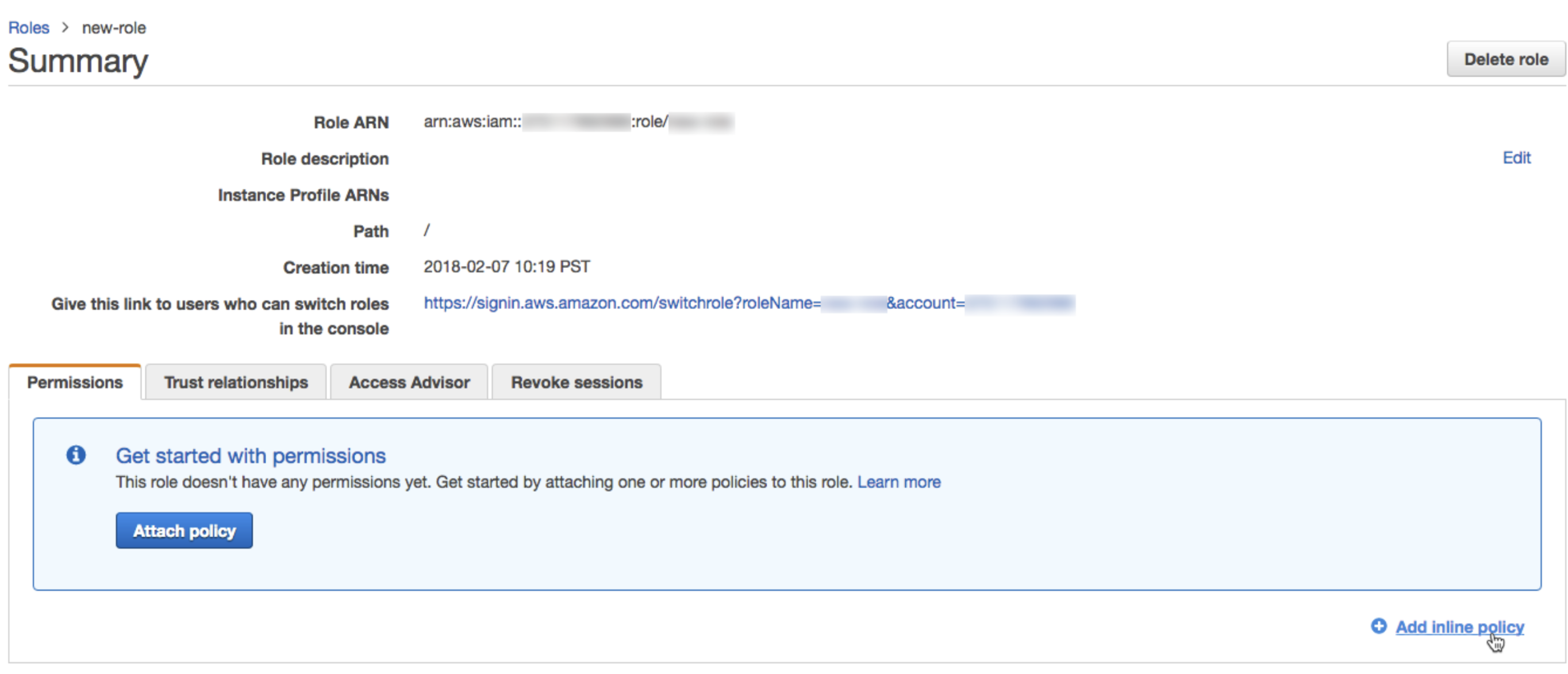
In the list of roles, click the role you created.
Add an inline policy.
a) On the Permissions tab, click Add inline policy.
b) In the policy editor, click the JSON tab.
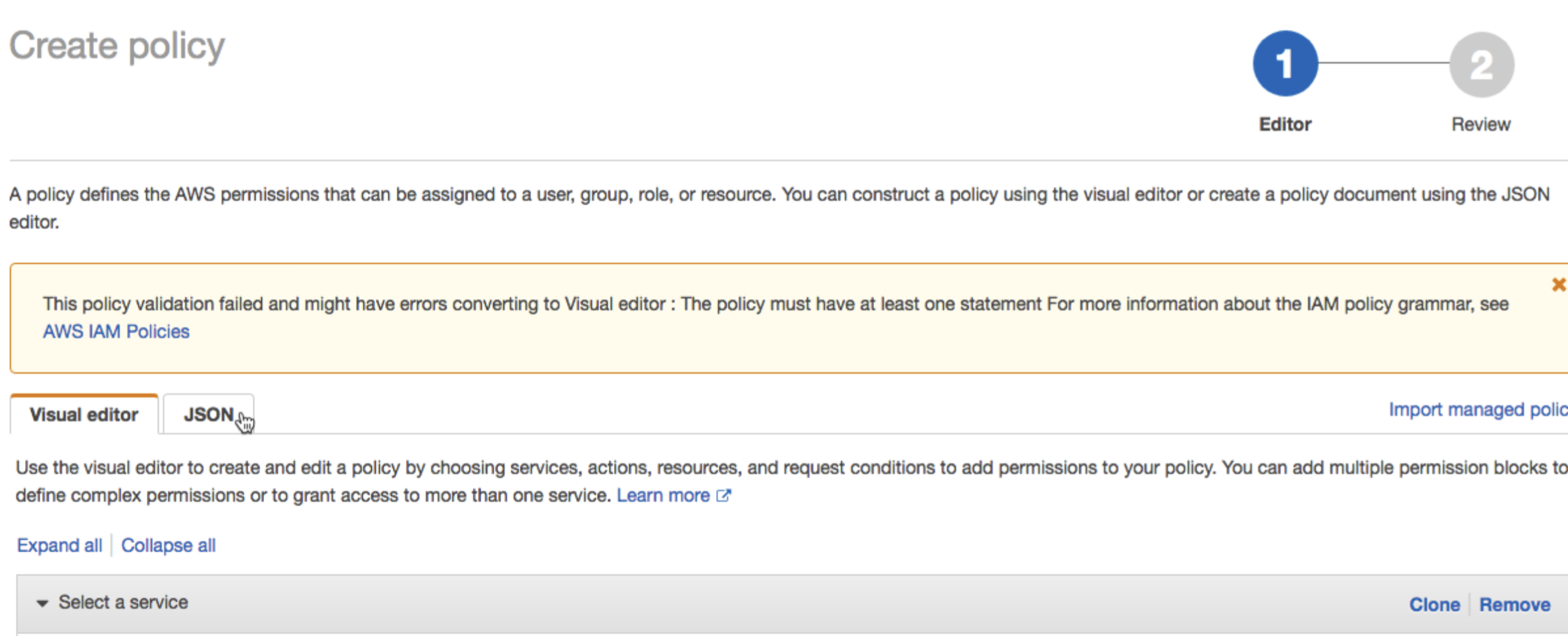
Copy the access policy to grant the role READ access to the bucket. Make sure to replace
<your-bucket>with the correct value.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1622505600",
"Action": ["s3:GetObject", "s3:ListBucket"],
"Effect": "Allow",
"Resource": ["arn:aws:s3:::<your-bucket>", "arn:aws:s3:::<your-bucket>/*"]
}
]
}
- In the role summary, copy the Role ARN.
- Please provide WhyLabs with this role ARN, bucket name and bucket region to access your data.
Note: if the data is protected by an AWS KMS, you’ll need to grant the IAM role above access to kms:Decrypt permission in the KMS access policy.

