WhyLabs SCIM Provisioning with Okta
SCIM is only available to WhyLabs Enterprise Plan customers. To get started, please contact our support team or email us at [email protected].
This section provides guidance for configuring the Okta SCIM app integration to work with WhyLab's SCIM V2 service for automated user provisioning.
Setting up App Integration
Browse the Okta App Catalog and choose the SCIM V2 app with Header authentication.
Click on the "Add Integration" button to add the app to your Okta organization.
Click Next and Done to finish creating the integration.
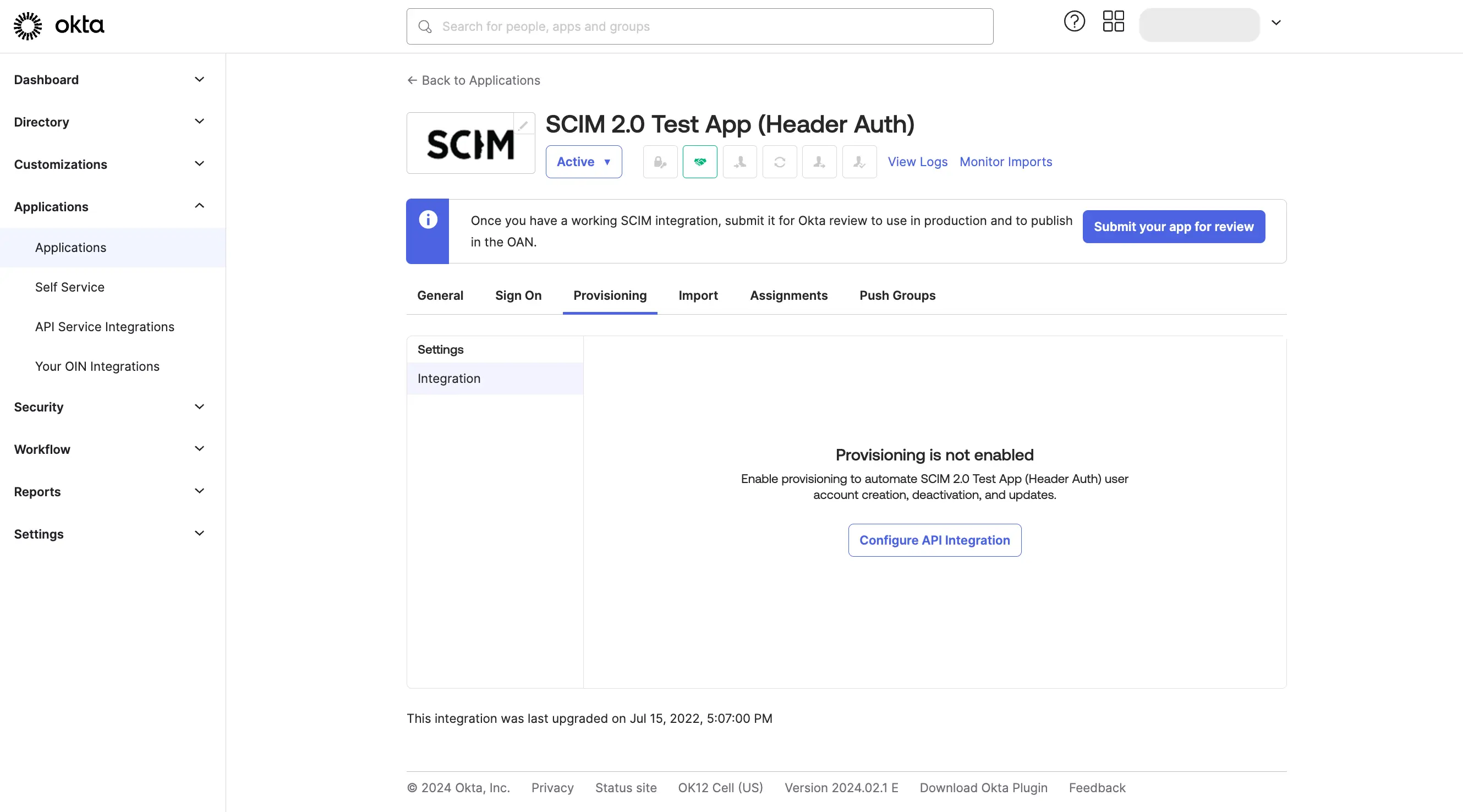
From the "Provisioning" tab, Click on the "Configure API Integration" button, and then Click "Enable API Integration".
Enter https://api.whylabsapp.com/scim as the base URL, and enter Bearer <API_KEY>
as the Authorization header value. Replace <API_KEY> with an account API key generated in your
account organization in the WhyLabs Access Token UI.
Click "Test API Credentials" to verify the connection.
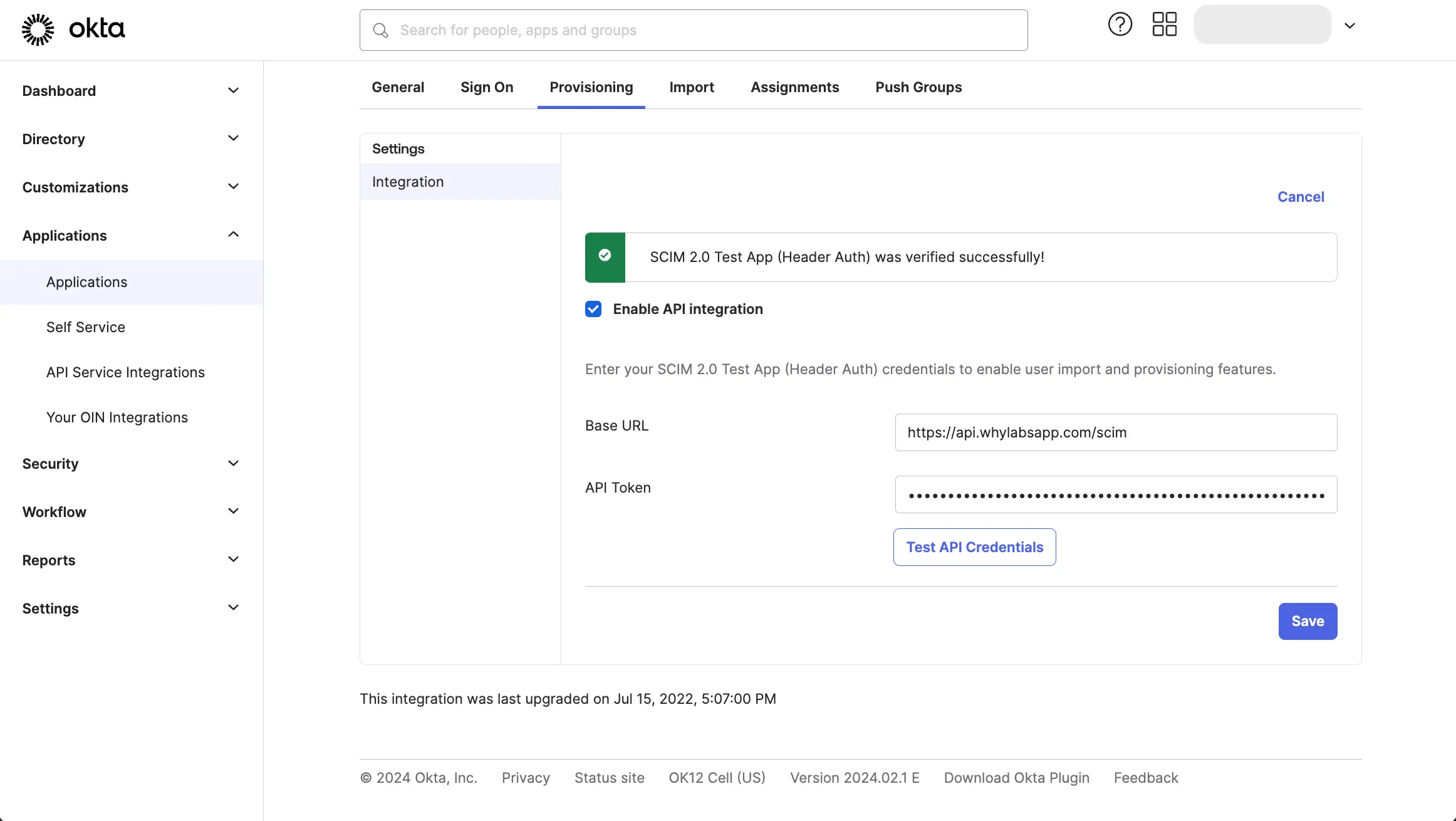
If you get Error authenticating: Unauthorized. Errors reported by remote server: make sure that you prefixed the API key
with Bearer , leaving a single space between it and the API key.
Configure App Provisioning
From the "Provisioning" tab, click on the "To App" tab and click "Edit". Enable the "Create Users" and "Deactivate Users" options and click "Save".
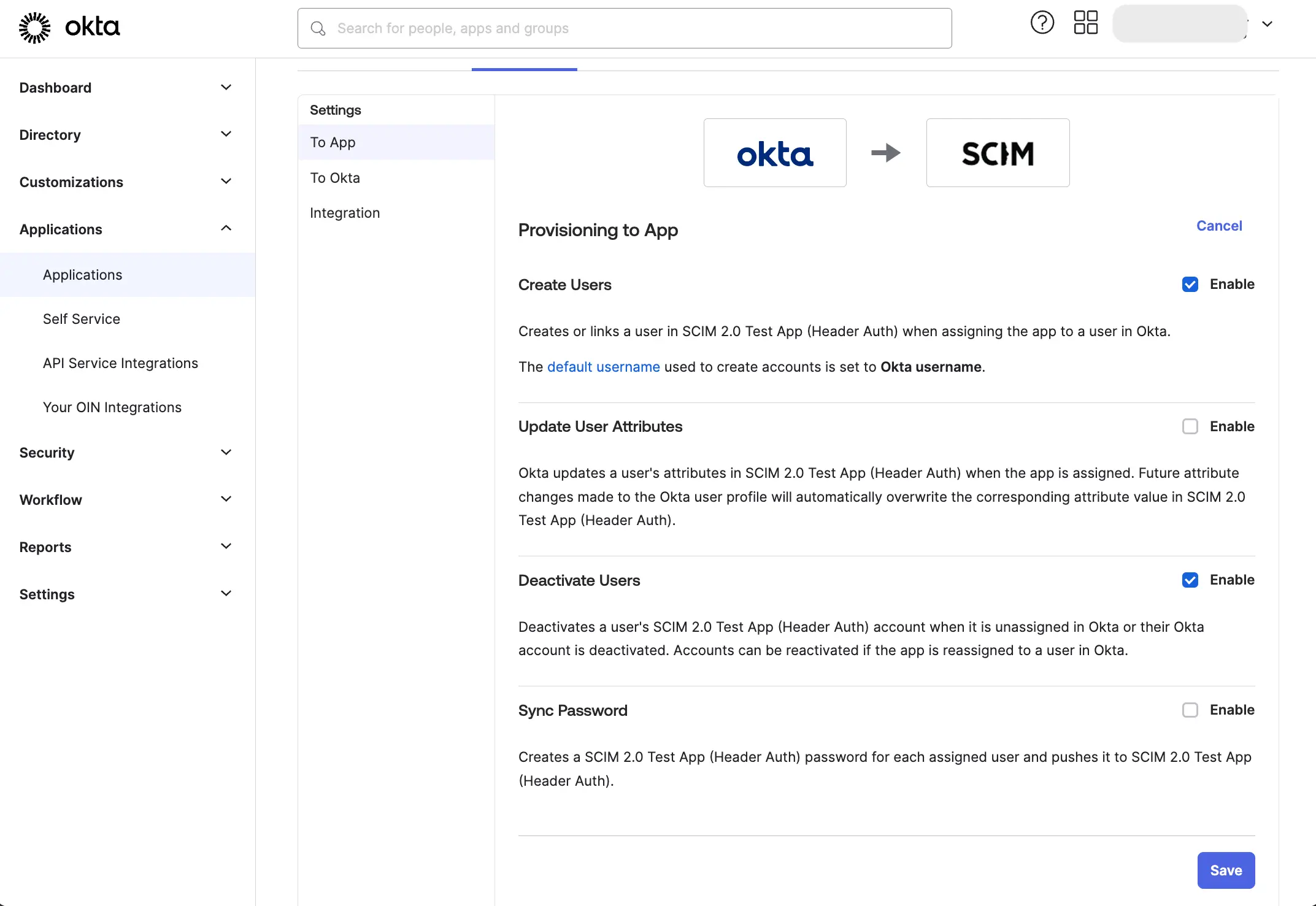
We do not recommend enabling the "Update User Attributes" option as WhyLabs does not support additional user attributes at this time. Do not enable the "Sync Password" option as WhyLabs does not support password synchronization.
Remove all "Okta" attribute mappings other than the required mappings, as shown below:
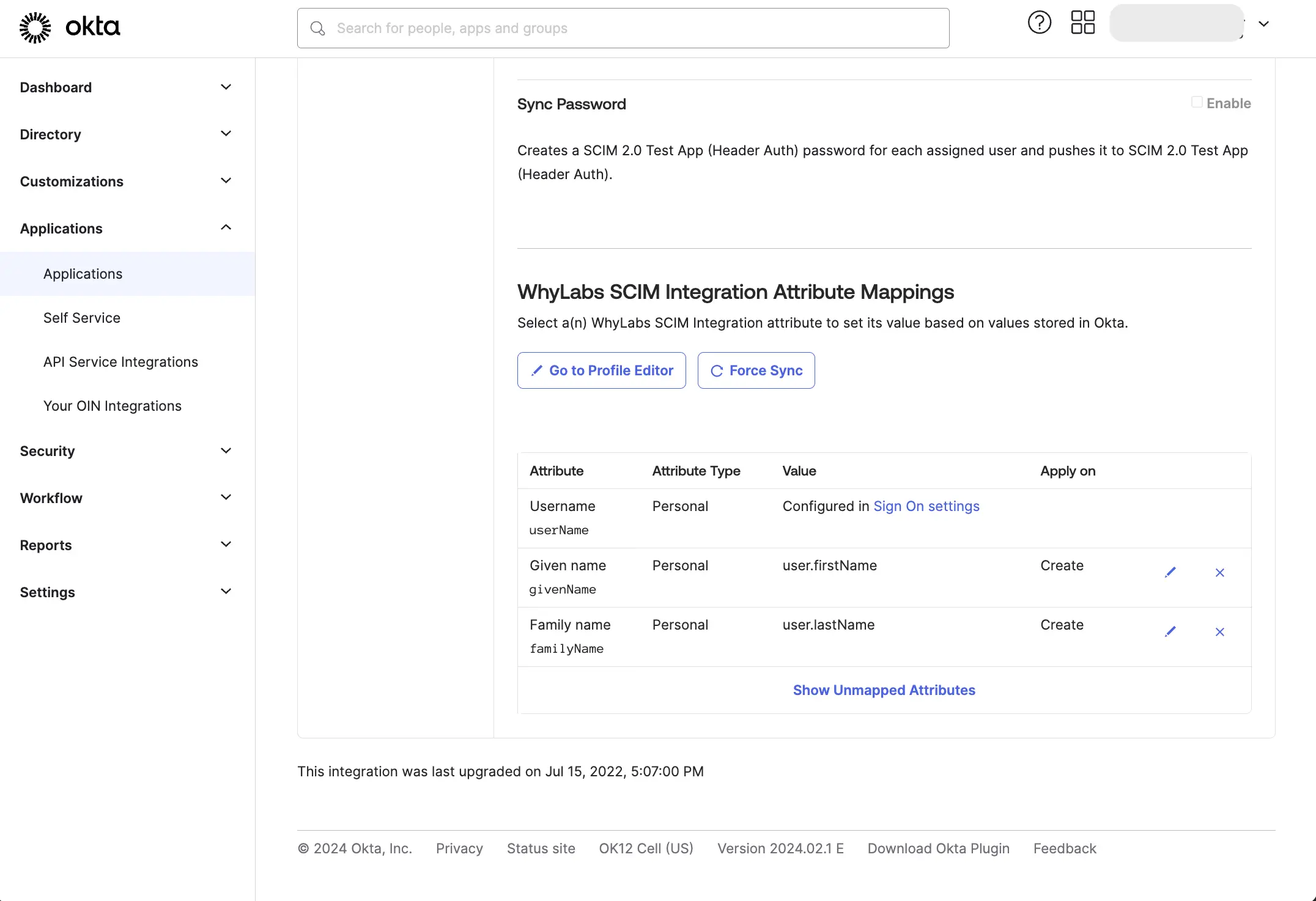
Pull existing users and groups from WhyLabs
From the "Import" tab, click "Import Now" to pull existing users from WhyLabs to Okta. Ensure that there is an existing Okta user for each WhyLabs user. Users in WhyLabs that do not have a matching user in Okta will not be managed by Okta.
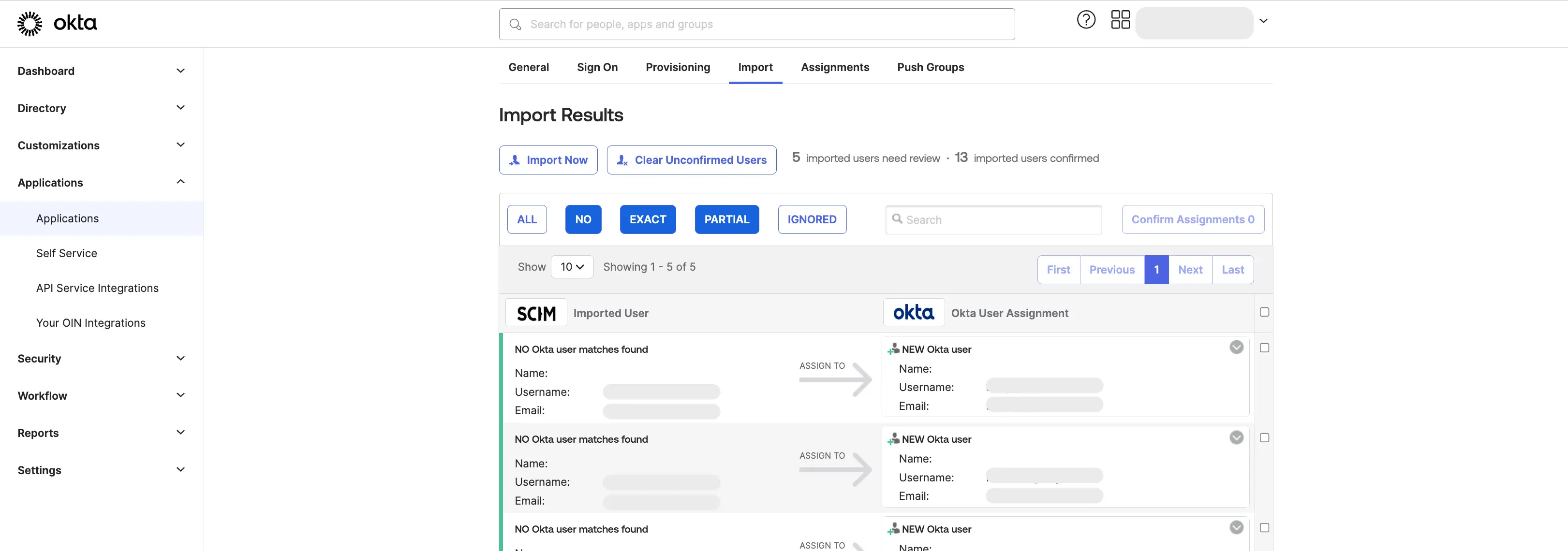
If there are users in WhyLabs that do not have a matching user in Okta, either create a new user in Okta or contact WhyLabs to remove those users from your account. You cannot create a new user from the Import tab, because WhyLabs does not have the first and last name attributes that are required by Okta.
Create an Okta group to manage WhyLabs users
Okta requires that users are assigned and provisioned to an app before they are assigned to groups, see Okta's documentation on App assignments and group push
We recommend you create one overall group to represent all users with access to WhyLabs, and then always add users to this group before assigning them to a WhyLabs membership group (see the following section).
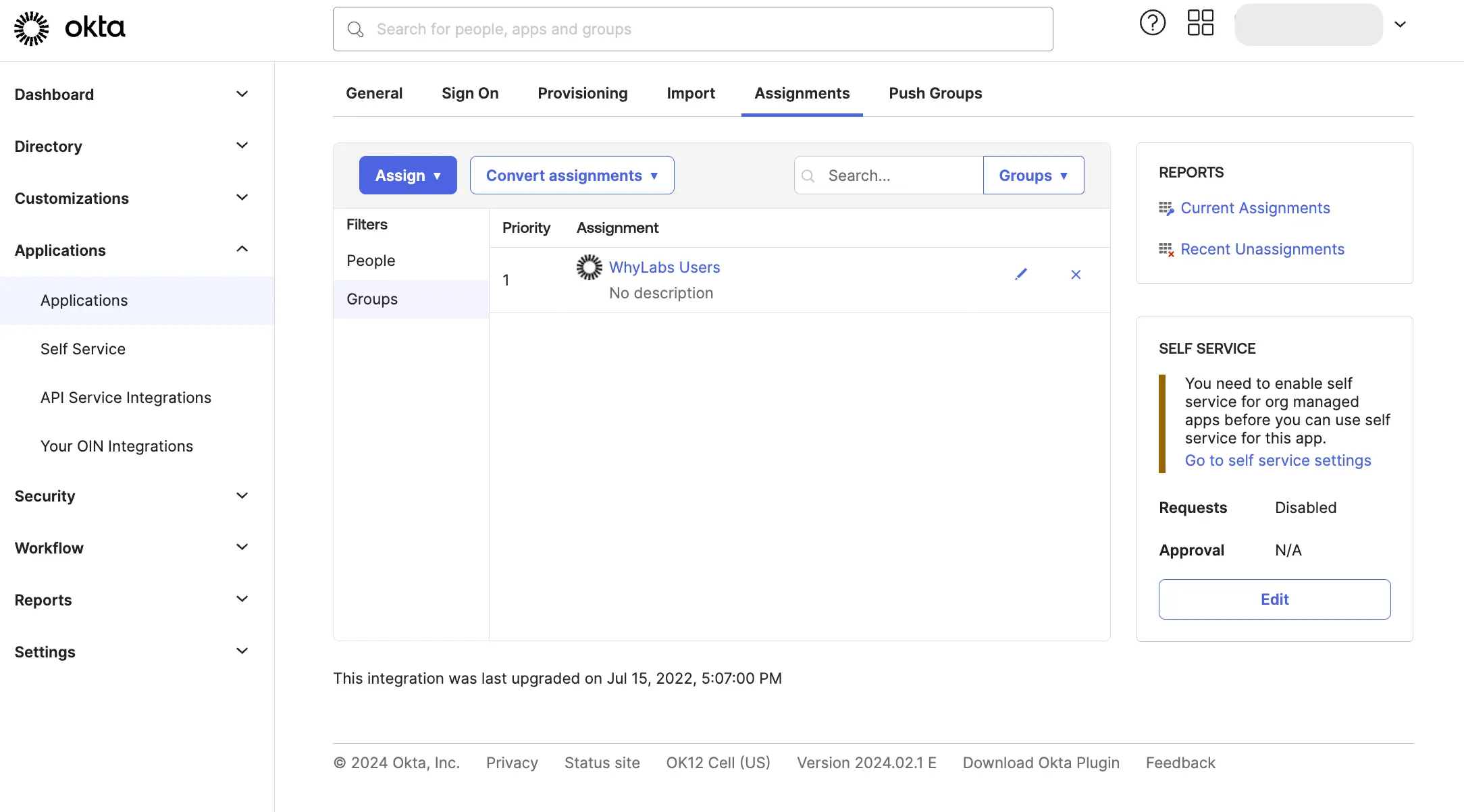
Go to the "Assignments" tab, and click "Assign" to assign the WhyLabs user group to the WhyLabs SCIM app.
Create Okta groups to manage WhyLabs memberships
Group Push is used to manage WhyLabs memberships in Okta. Push Groups are Okta groups that are each linked to a WhyLabs SCIM group of the same name. Changes to user assignments in the Okta group are pushed automatically to the corresponding WhyLabs SCIM group.
SCIM groups are created in Okta automatically. You can refresh these groups by clicking "Import Now" in the "Import" tab, or using "Refresh App Groups" in the "Push Groups" tab.
The WhyLabs group names take the form whylabs-<orgId>:<role>, for example the Member role in org-3454 is
represented as the SCIM group whylabs-org-3454:member.
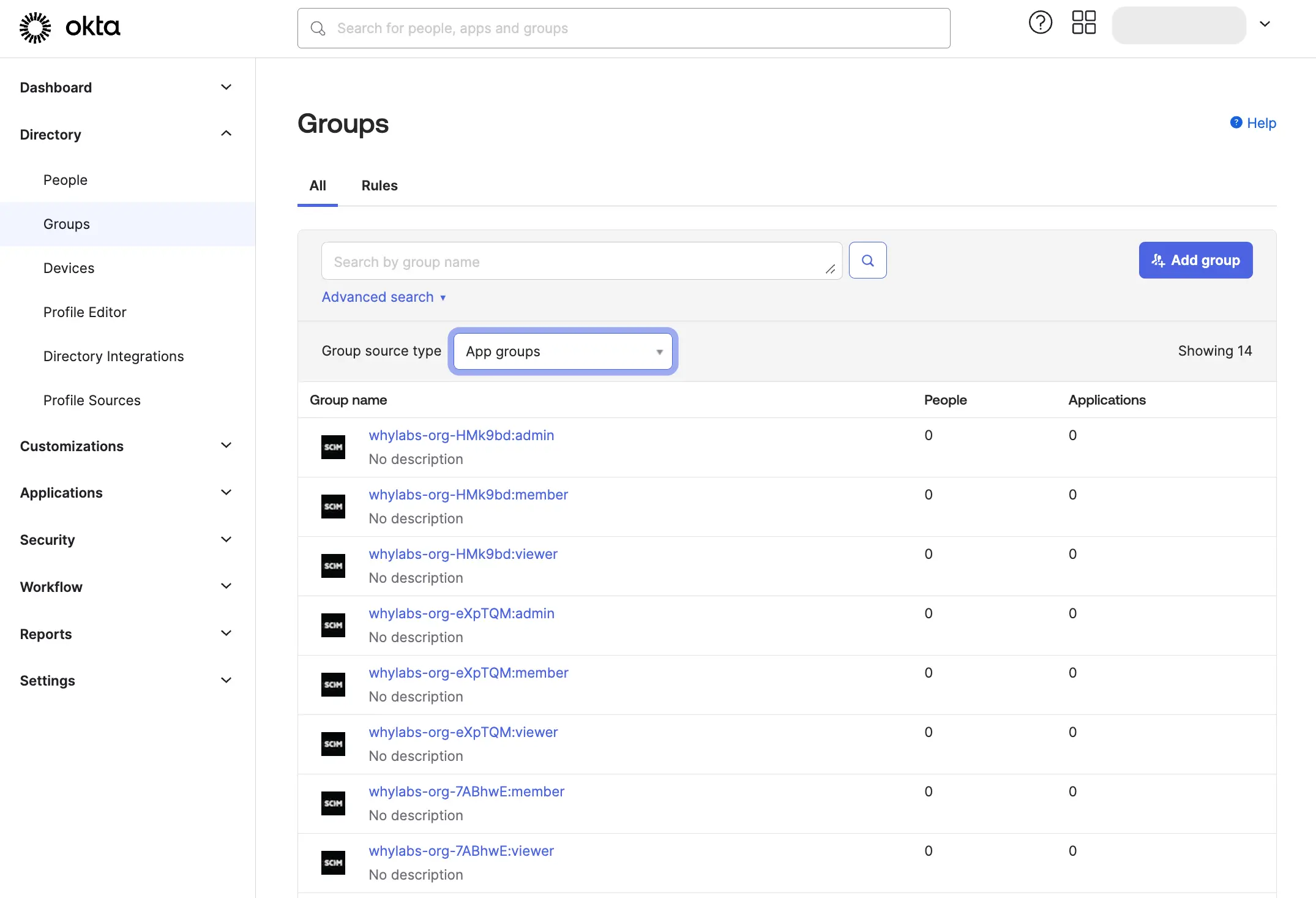
You can see these groups in the "Groups" tab using the "App Groups" filter.
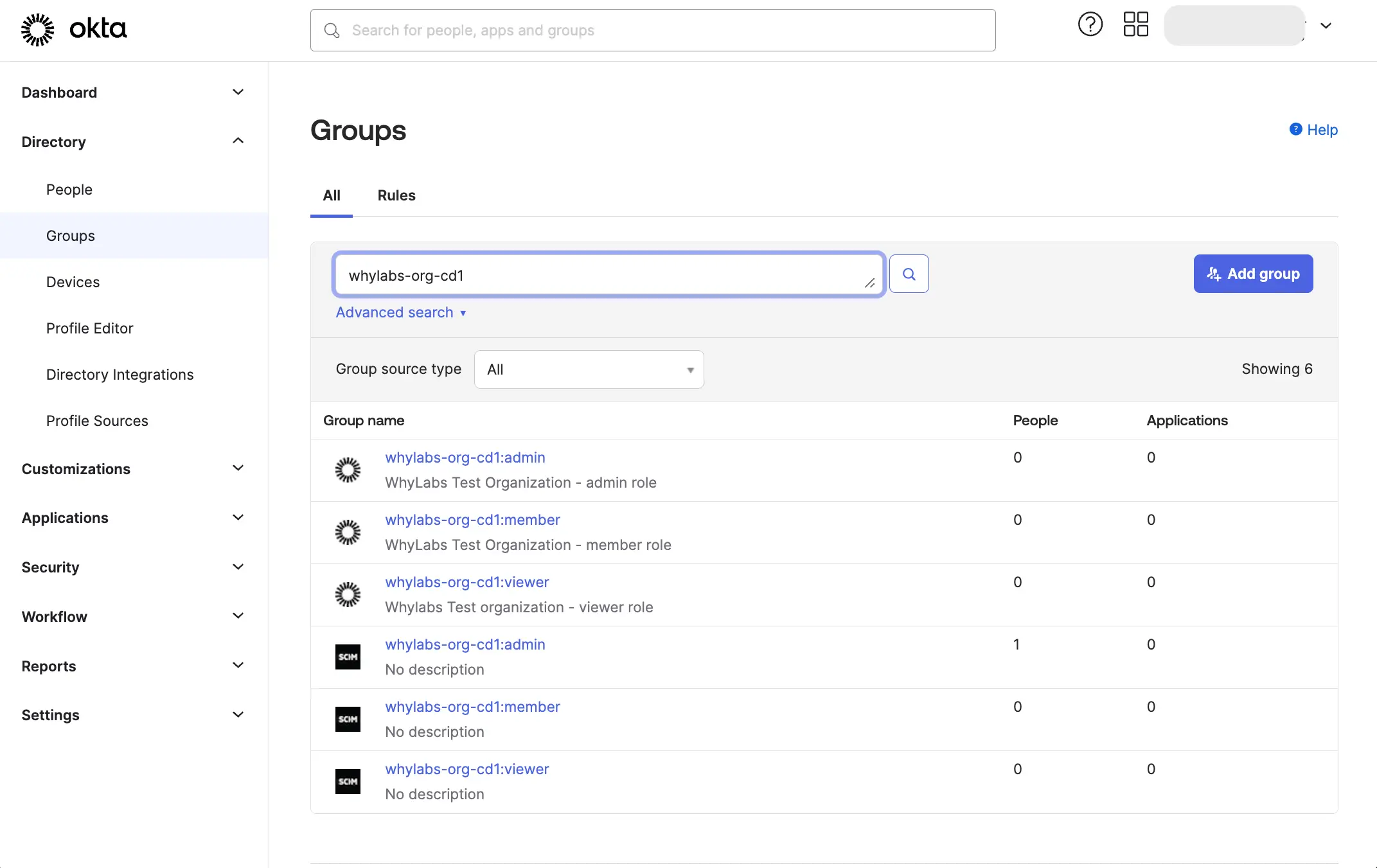
Create groups with names that match the WhyLabs SCIM group names exactly, and assign users to these groups.
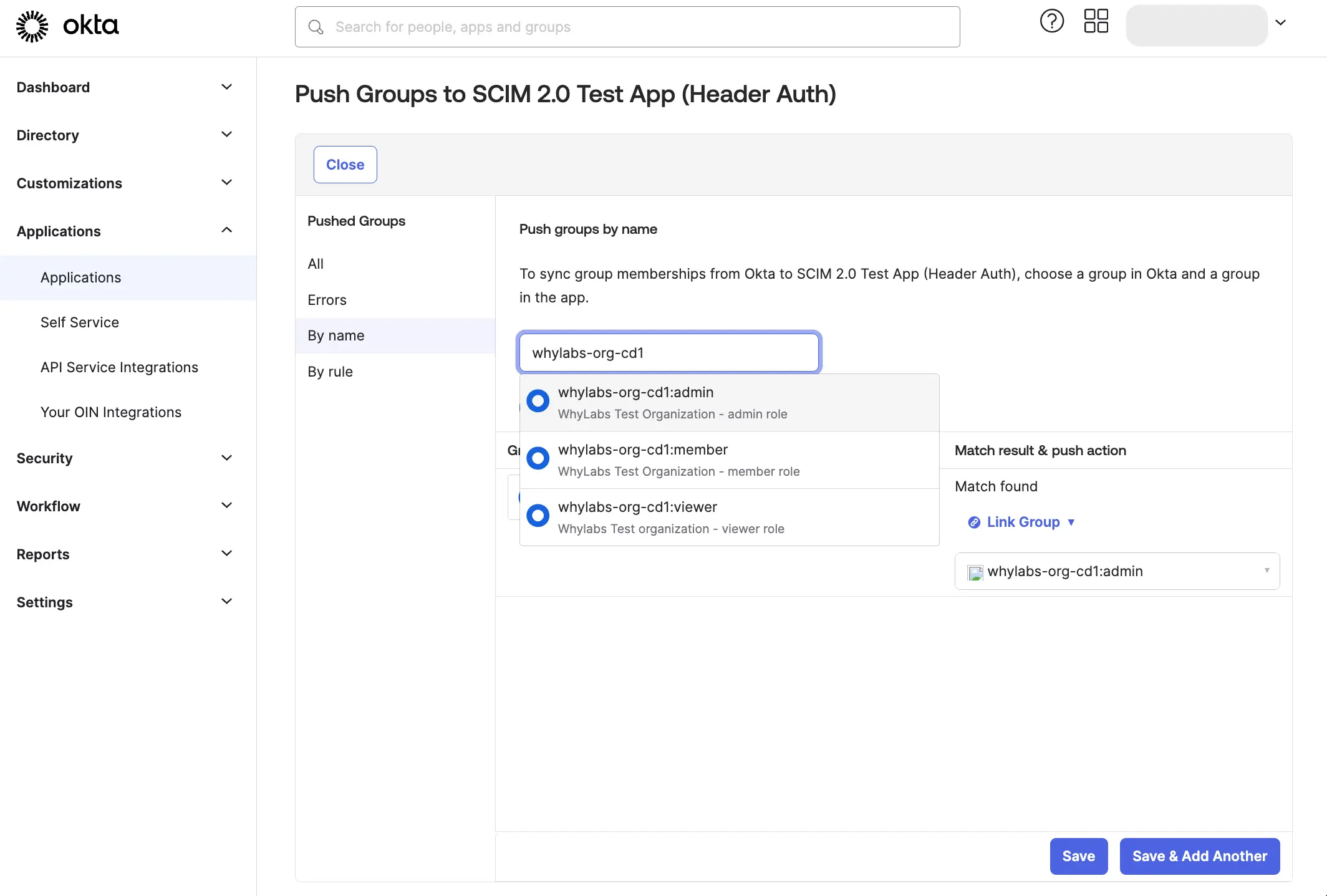
On the "Push Groups" tab, click "Push Groups" and link each WhyLabs Okta group to the corresponding WhyLabs SCIM group.
Observations on provisioning behavior
When adding a new user to WhyLabs, always assign that user to the WhyLabs SCIM app before assigning them to a specific WhyLabs membership group. If you do not do this, there may be a delay in provisioning the user to WhyLabs, or the user may not be provisioned at all.
When removing a user from WhyLabs, always remove the user from the WhyLabs membership group in Okta before removing
It is not possible to rename, create or delete WhyLabs groups.
Within WhyLabs, a user can only be assigned to one role in any specific WhyLabs organization. If a user is assigned to more than one SCIM group with the same WhyLabs organization ID, the user's role may change unexpectedly whenever one of the groups is pushed by Okta.

