WhyLabs SAML Provisioning with Okta
SAML Integration is only available to WhyLabs Enterprise Plan customers. To get started, please contact our support team or email us at [email protected].
WhyLabs supports SAML (Security Assertion Markup Language) based Single Sign On (SSO) through providers such as Okta. Configuring for your WhyLabs account lets your organization log in to WhyLabs using credentials stored in an Okta identity store that has been configured with a SAML Identity Provider. In order to allow your Okta users to log in to WhyLabs, you will need to create a SAML Okta application and provide WhyLabs with its sign-on URL and certificate. You can find more detailed instructions about this process in the official Okta documentation
Steps
- Visit
https://{YOUR-OKTA-TENANT}-admin.okta.com/admin/apps/active - Choose “Create App Integration”
- Pick “SAML 2.0” and click “Next”
- Name your app something descriptive, e.g. “WhyLabs AI Control Platform”
- Adjust the app logo and visibility settings as needed
- Click “Next”
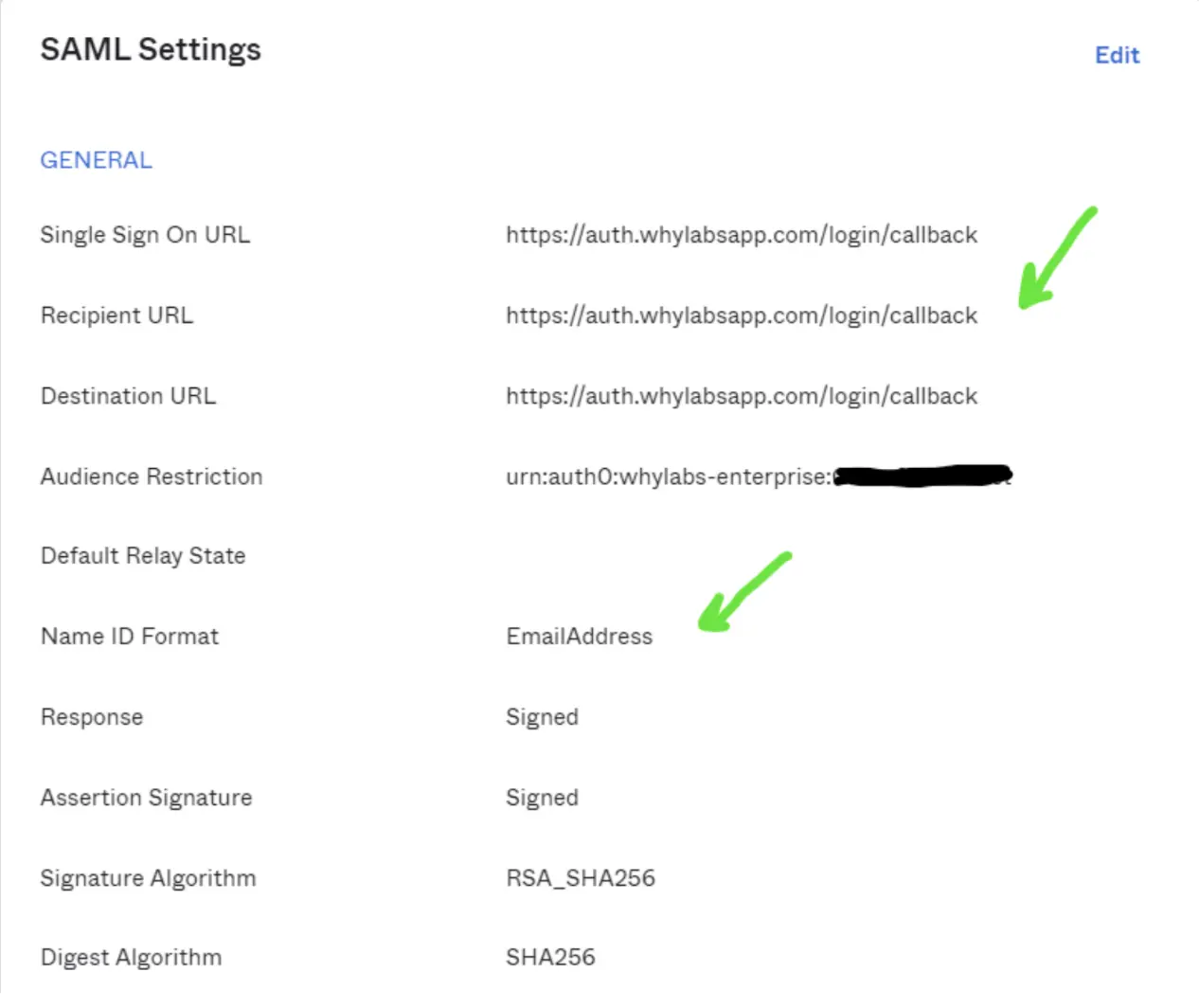
- Set the “Single sign on URL” to
https://auth.whylabsapp.com/login/callback - Set the “Audience URI (SP Entity ID)” to the value provided by WhyLabs which should look similar to
urn:auth0:whylabs-enterprise:{APPLICATION-NAME} - Set the “Name ID format” to
EmailAddress - Leave the other options unchanged and click “Next”
- Select “I'm an Okta customer adding an internal app”
- Fill out the Okta setup feedback form below (optional) and click “Finish” 13. Go the the “Assignments” tab and add users or groups that should have access to WhyLabs
- Go back to the “Sign On” tab
- Scroll down to find the “SAML Setup” section on this page (next to “SAML Signing Certificates”) and click “View SAML setup instructions”
- On this page, note the “Identity Provider Single Sign-On URL” and the “X.509 Certificate” sections
Please copy the Sign-On URL and download the certificate, then forward both to WhyLabs via email. We will let you know once the connection has been set up on our end and is ready for testing.
Your app’s SAML settings should look roughly like this in the end: